Tyler's Blog
🐧 WGU C851 - Linux Foundations / LPI Linux Essentials
Written by Tyler on June 15th, 2022 at 10:29 pm.Just wrapped up my Linux Essentials certification! This class was a super quick one for me, since I've been using Linux on a daily basis for almost a decade. To be safe, I attempted all of Jason Dion's practice exams on Udemy to verify I knew what would be on the exams and consistently got 90%+. All in all, this was easily the quickest test I've ever taken - 40 questions and I wrapped it up in under 5 minutes.
Up next, cryptography class!
🎣 Configuring Exchange 365 to Whitelist Phishing Simulations
Written by Tyler on June 10th, 2022 at 5:23 pm.I'm working on setting up Gophish for some internal phish testing at my workplace. Gophish is an open source phishing simulation tool written in Go (who'da thunk?) that allows administrators to schedule phishing campaigns to test their employees. Think of KnowBe4, but free and without the salespeople spamming your email and voicemail.
One of the hurdles I ran into while setting up our simulation was the increased security of Exchange Online in comparison to on-premise. Previously, when I configured KnowBe4, the company I worked for self-hosted their mail server - all we had to do was whitelist anything coming from their IP addresses with a certain header. Nowadays, it's a tad more involved. Most tutorials tell you to gather a list of all of the fake email addresses you'll be using, in addition to the other information - a time consuming process. There is still a way to get around this, thankfully.
Overview
There are a few steps that need to be done in order to ensure delivery - I'm assuming you already have Gophish and Postfix configured in your environment. I may write a bit about setting this up in another post - but it's outside of the scope of this post.Here's the broad overview of what we need to do:
- Configure the sending email server to "spoof" envelope address
- Whitelisting the "spoofed" envelope address on Phishing Simulations page
- Implement transport rule to strip header showing "spoofed" address.
Configuring Postfix to Spoof Envelope Addresses
In my setup, I chose to use Postfix as our sending mail server instead of just using our 365 tenant. Exchange 365 REALLY does not like you modifying your from address in any way whatsoever, so this was a necessary step. I configured Postfix to only accept local connections (127.0.0.1) and to "spoof" it's from address. I'm putting "spoof" in quotes because we're really forcing Postfix to use it's actual address.Here's what I added for the envelope modifications:
/etc/postfix/main.cf
sender_canonical_classes = envelope_sender
/etc/postfix/canonical
sender_canonical_maps = regexp:/etc/postfix/canonical
/.+/ [email protected]
The canonical file only contains one mapping, which matches any address. This will force Postfix to use our address instead of the fake one we're using in our phishing tests.
Whitelisting the Internal Mail Server
Here's how to get to the page we're looking for. Don't worry, here's a direct link to the page: Phishing Simulation- Open Microsoft 365 Defender: https://security.microsoft.com
- Navigate to Policies & rules under Email & collaboration.
- Pick Threat policies on the Policies & rules page.
- Pick Advanced delivery under the Rules header.
- Finally, pick the Phishing simulation tab.
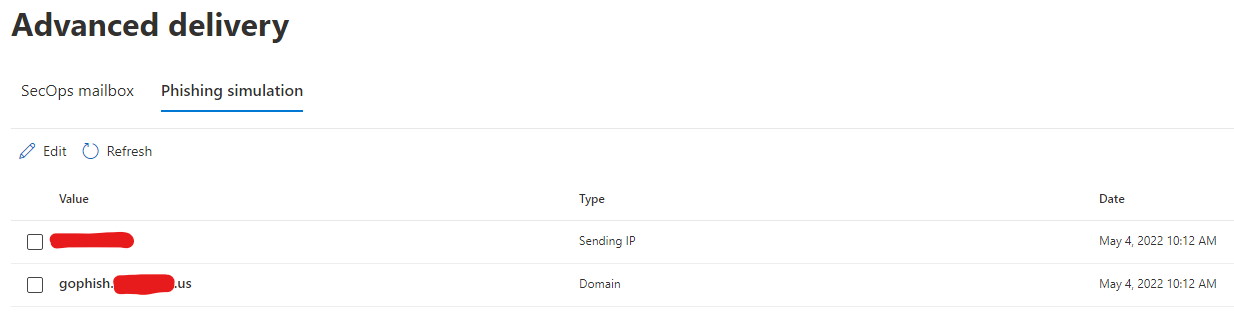
On the phishing simulation page, you'll need to add the domain and an IP address for your on-premise mailserver. This needs to match what you've configured your mail server to use as it's envelope address! I've also added a public "gophish" A record on our domain pointing to the same IP address so everything is hunky-dory.
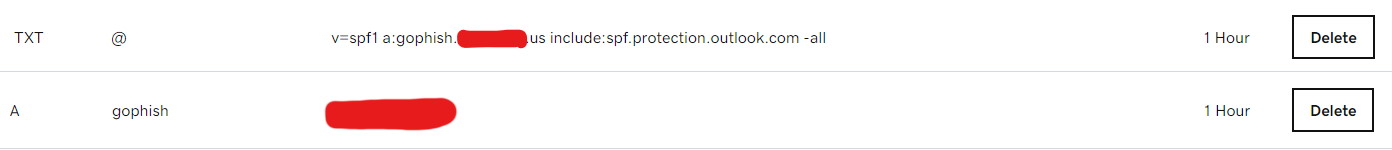
Implement Transport / Mail Flow Rule
The next piece required for this to work is removing the Authentication-Results header. I'm accomplishing this with a transport rule. Without this step, mail will still get delivered, but Outlook will show the "spoofed" domain after the phishing domain, like this: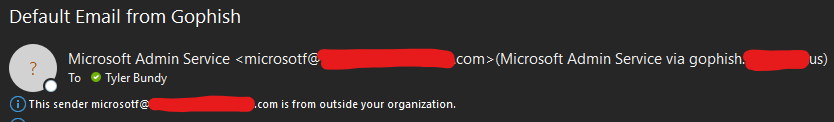
To create transport rules, you'll need to open the Exchange 365 admin center and pick Rules under the Mail flow header on the left. Here's a direct link for your convenience: https://admin.exchange.microsoft.com/#/transportrules
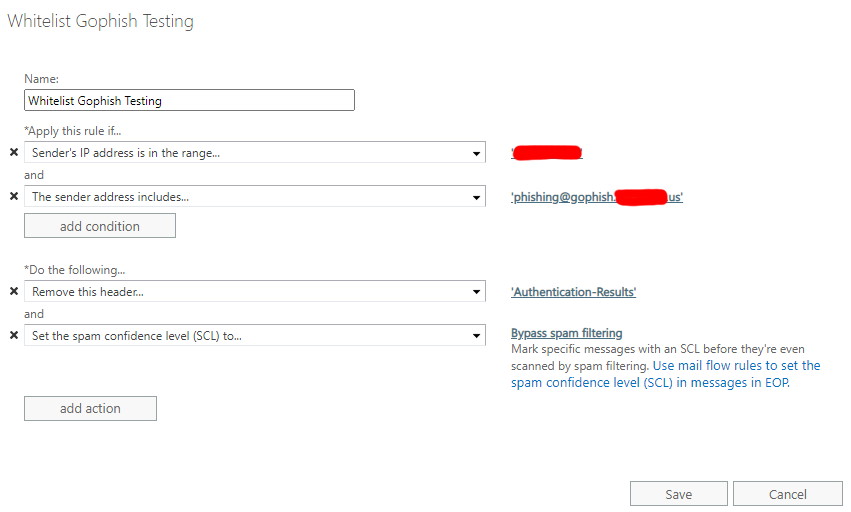
The rule I created matches the sending IP Address (same address specified in the DNS A record and Sending IPs earlier) and the envelope address. You can also added a header check as a security-through-obscurity measure, if you desire. The setting of the SCL score to -1 may not be entirely necessary since we also configured the phishing simulation whitelist, but you can never be too sure, can you?
🎓 WGU D114 - Implementing and Administering Networking Solutions / CCNA
Written by Tyler on June 8th, 2022 at 11:06 pm.I just wrapped up my CCNA 220-301 exam! This was not as difficult as I expected, quite honestly - I got myself hyped up because of the weight WGU assigns this class (6 vs the usual 3-4) but it was essentially a more vendor-specific version of the Network+, with some more protocols and networking technologies covered.
I spent around a month and a half on this class - I watched the majority of the CBTNuggets CCNA Course hosted by Jeremy Cioara and Keith Barker - this gave me a great overview of all of the concepts covered by the exam objectives. I used the Boson ExSim-Max practice exams to test myself for a few days before the exam. I also used the Cisco practice exams included with my tuition. I was consistently passing the Cisco exam and mostly passing the Boson exams. The ability to only retake questions I missed on ExSim was incredibly useful during my final week "cram" period.
All in all, the actual exam was a bit of a let down - most of the complex topics I covered in the practice exams weren't covered on the exam. I won't delve deeper into it since there's an NDA, but I definitely feel less like an idiot after passing the exam. Maybe I am a network engineer after all? Up next, Linux Essentials. I'm going to try to pass this one quick.

Hey there! I'm Tyler.
Hey there! My name is Tyler, and I'm an experienced infrastructure engineer, web developer, and cloud administrator.
I have over 8 years of experience supporting companies of various sizes with their networking and support needs.
I am currently going back to school in an effort to earn my bachelor's degree in Network Operations & Security.
I am also a small business owner providing web design, hosting services, and other I.T. consulting offerings to my client-base of over a dozen.
I write about a bit of everything - technology, my hobbies, electric vehicles, and whatever else piques my interest.