Tyler's Blog
🧠 Cioara's Three Step Subnetting
Written by Tyler on May 4th, 2022 at 12:17 am.I'm studying for my CCNA certification and am finding myself knee deep in subnetting again - my Network+ subnetting method must've fallen out of my brain, so I'm making myself write the method down for my own future reference.
These methods are taught by Jeremy Cioara and makes the most sense to me compared to the other methods I've seen.
I highly recommend Cioara's materials on the CBTNuggets training site if you are willing to shell out the money - I'm watching all of the CCNA content in an effort to hammer the networking fundamentals into my head.
Anyways - this assumes you know how to represent base-10 numbers in base-2/binary - if not, this is probably going to make absolutely no sense. Here's my best attempt at a brief explanation:
Understanding Binary
Binary is based on 1s and 0s - ons and offs. Each number (bit) represents a power of 2. Since we're talking about IPv4, we're limited to 8-bit numbers, which allows for a maximum value of 255.Like base-10 numbers, each digits represents a power - we're used to the power of 10s (10^0 = 1, 10^1 = 10, 10^2 = 100, 10^3 = 1000, etc.), but the same idea applies to binary - just with 2s instead of 10s.
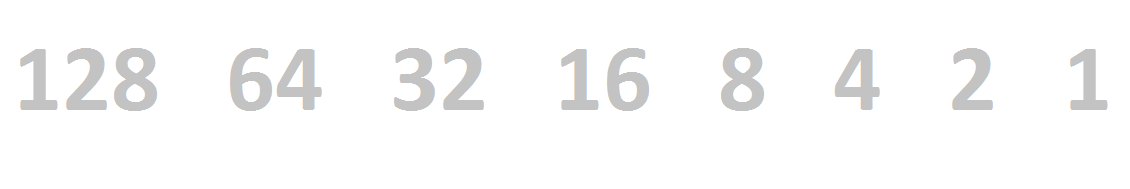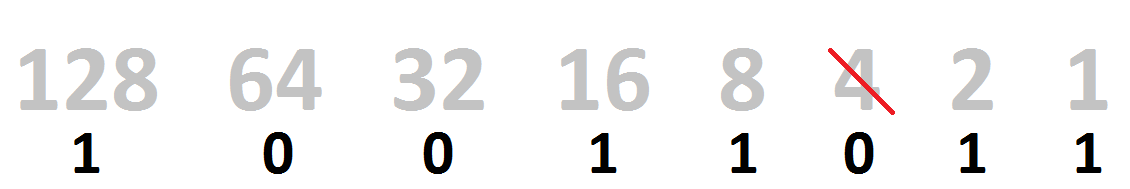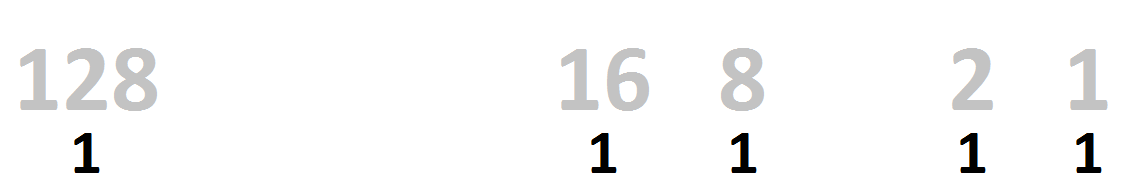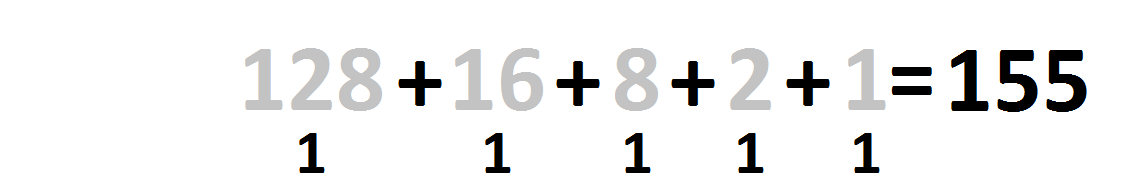
To convert back to something we can understand, we need to add the values together. Remember - the number is read from right to left, so the leftmost bit represents 128 and the rightmost represents 1.
- Each bit represents a power of 2. For an 8-bit number:
- 2^7 = 128
- 2^6 = 64
- 2^5 = 32
- 2^4 = 16
- 2^3 = 8
- 2^2 = 4
- 2^1 = 2
- 2^0 = 1
- Wherever there's a 1, add the power of 2 it's representing.
- 10011011 = 155
- 00101111 = 47
- 11111111 = 255
- 10000001 = 129
Anyways, on to the meat and potatoes of my rambling:
🏢 Three Step Subnetting - By Number of Networks
-
Convert the number of desired networks to binary, count the bits.
Let's say we were trying to split 200.5.1.0/24 into 50 seperate networks. We would convert 50 into binary:128 64 32 16 8 4 2 1 0 0 1 1 0 0 1 0
50 expressed as a binary number is 110010, so we'll need 6 bits to represent it. -
Reserve the bits in the given range's mask and find your "increment".
We're starting with a /24 (255.255.255.0) subnet mask. Since we're focused on the number of networks we're creating, we need to append our bits onto the starting mask:
11111111.11111111.11111111.XXXXXX00
This means that we have 2 bits left over for host addressing. Now, for the increment - this value is determined by the last network bit in the mask we just created. Our last bit lands in the 4 spot in the final octet, so our increment is 4.
One thing to note here - we're already starting with 1 network, so we really only need to subnet out 49 hosts. This would be particularly important if we're doing a power of two - e.g. if we want 8 networks, we need to borrow 3 bits, not 4 - we only need 7 additional networks. -
Use the increment to generate network ranges.
Start with the network address given and add the increment in the octet we mentioned previously.
- 200.5.1.0 - 200.5.1.3
- 200.5.1.4 - 200.5.1.7
- 200.5.1.8 - 200.5.1.11
Not too bad, right? I think the stockholm syndrome must be kicking in...
🖥 Three Step Subnetting - By Number of Hosts
-
Convert the number of desired hosts to binary, count the bits.
The process is pretty similar to what was mentioned above, but since we're focusing on hosts we count from the right instead of the left, making sure to reserve enough bits to properly express the number of hosts we want in each subnet.
For example, let's say we are subnetting 192.168.5.0/24 into blocks of at least 23 hosts. Since we lose two hosts to the network and broadcast addresses, we would convert 25 into binary:128 64 32 16 8 4 2 1 0 0 0 1 1 0 0 1
25 expressed in binary is 11001, so we need 5 bits. -
Reserve the bits in the given range's mask and find your "increment".
We're starting with a /24 (255.255.255.0) subnet mask. Again, since we're focusing on hosts, we need to reserve the last 5 bits:
11111111.11111111.11111111.000XXXXX
Since we only needed 5 bits to represent our hosts, we can fill the remaining 3 bits with 1s for the network portion. This will give us a subnet mask of /27. Our increment is on the bit representing 32 in the last octet, so that's our increment. -
Use the increment to generate network ranges.
Start with the network address given and add the increment in the octet we mentioned previously.
- 192.168.5.0 - 200.5.5.31
- 192.168.5.32 - 200.5.5.63
- 192.168.5.64 - 200.5.5.91
Anyway, that's it. I'm sure I will forget subnetting again after I pass my CCNA, but at least now I have something I can look back at. In that case - hopefully I got it right!
I have the bulk of my unedited notes on this uploaded here for your reading displeasure: subnetting.txt
⚡ 2022 Northfield Earth Day Event
Written by Tyler on April 23rd, 2022 at 9:17 pm.This weekend, Northfield hosted an Earth Day event and I, along with three other EV owners, were invited out to talk about our cars. Despite the rain, turnout was pretty good! We got to talk to a few dozen people who were curious about our experiences, and answered any questions they may have had for us.
I personally love attending these events - the people we talk to are often on the fence about purchasing an EV for their next vehicle, so letting them sit inside and interact with the car helps them to make an informed decision. Getting "butts-in-seats" is the ticket to getting people to make the switch. It certainly was for me, anyway! Once you get to floor the accelerator there's no going back.
04/22 - Northfield Earthday Event
These events are always a lot of fun - getting to meet new people and share our experiences always puts a smile on our faces!
🎓 WGU C178 - Network and Security Applications / CompTIA Security+
Written by Tyler on April 16th, 2022 at 8:32 pm.Whew, this was a tough one. I just completed my CompTIA Security+ certification exam! I am writing this post to document my journey towards earning my bachelor's degree from WGU. I tried to cram for this exam early on and ended up almost burning myself out, so I have definitely learned to slow down and make time for leisure between multiple days of study. Shout out to Professor Messer again for the awesome free and paid content! I would not have been able to understand some concepts covered on the exam if it weren't for your videos.
This exam was a bit more difficult for me compared to either of the A+ or the Network+ exams. I understood the core concepts - but only to the level at which I taught myself during my career up to this point. There were a lot of terms that I needed to hammer the definition of into my head.
- Cybersecurity Threats / Vulnerabilities - This section covers a bunch of types of malware, attack types, threat actors, pentesting, vulnerability scanning, and impacts. This was a fun section for me - my time spent participating in the Collegiate Cyber Defence Competetion back when I was earning my Associate's degree prepared me for a lot of the terminology used here. The Red / Blue / White teaming is a fun concept I encourage any prospective cybersecurity candidate to take part in.
- Technologies / Tools - This area covers, well, technology and tools. A lot of the technologies covered are either hardware or software network appliances - routing/switching, firewalls, IDS/IPS tools, etc. I have a bunch of experience with network infrastructure - I was a network technician straight out of college and am now responsible for my company's entire network stack, so this area was something I understood already. The tools portion of the exam was a bit new to me - I haven't worked with a bunch of the pentesting tools up until now, pretty much only netmap.
- Architecture / Design - This section covers building secure network architecture and compliance / configuration frameworks, along with physical security and resiliency. As a network engineer, I have already interacted with a good portion of the things mentioned here. The Security+ builds on the concepts mentioned in the Network+ exam - e.g. DMZs, Honeypots, loadbalancing, virtualization/sandboxing, and VPNs. Software defined networking is also briefly covered, but I have had no prior experience working with SDNs so that was a pain point for me. The network resiliency piece coveres both loadbalancing/high availability and the ability to recover from incidents quickly. Non-persistant computing and imaging/cloning is covered here. I developed a tool for my company to use for capturing and deploying images using DISM and Windows PE, so I understood a lot of the core concepts here already.
- Identity / Access Management - This piece covers managing users - verifying who they are, their access level, and keeping track of their actions. I have provisioned AAA services in the past so this built upon the tidbit of experience I already have from work. All kinds of technologies are covered here - WiFi security, 802.1X/NAC, multi-factor authentication, and physical access controls like smartcards and biometric readers to name a few.
- Risk Management -
This was probably the most difficult section for me. This section touches on the decisions businesses have make regarding risks - how to prepare for them, how to respond, and how to recover from them.
Incident response was the easiest piece for me - I've had to deal with malware outbreaks previously. The risk management side of things, however was something I had not really touched on before.
Disaster recovery is the most "exciting" piece for me - conceptualizing network redundancies, carrying out contingency plans, and getting everything back online. Definitely challenging and rewarding work! Also covered are various security practices, like data destruction and retention.
The compliance aspect is something I have experience with at my current job - we have to keep all sorts of financial records, phone recordings, and email archives for various lengths of time and ensure that they are readily accessible if an audit were to happen. Proper disposal is also important - especially with the type of information we deal with at my current employer. Physical destruction of hard drives is a lot of fun. - Cryptography / Certificates - This was a strong one for me. I have a bunch of experience with webhosting and webdesign because of my side-business, so PKI is something I work with on a regular basis. WiFi security is also touched on here - the different cryptographic and authentication protocols, some 802.1X and RADIUS as well.
The hardest part of this exam was memorizing all of the different acronyms. I had a a modicum of experience in most of the topics the exam covers... but I had never seen some of the defintions used in the way that they were. I had seen a lot of the actual definitions, but never shorthand.
I went over every section of the CertMaster Learn and CertMaster Practice that WGU includes with this class and I was still having trouble retaining all of the information, so I bought Professor Messer's Security+ Practice Exams to ascertain my knowledge level. After I scored pretty well on the three included exams, I scheduled my certification exam.
I passed my exam and earned my certification with a score of 782/900. This was bittersweet for me - I am glad I was able to pass, but I think I will continue to study the concepts covered in this certification though since there are still some concepts I am not 100% comfortable with.
Next up, CCNA. Wish me luck!

Hey there! I'm Tyler.
Hey there! My name is Tyler, and I'm an experienced infrastructure engineer, web developer, and cloud administrator.
I have over 8 years of experience supporting companies of various sizes with their networking and support needs.
I am currently going back to school in an effort to earn my bachelor's degree in Network Operations & Security.
I am also a small business owner providing web design, hosting services, and other I.T. consulting offerings to my client-base of over a dozen.
I write about a bit of everything - technology, my hobbies, electric vehicles, and whatever else piques my interest.